AIP US’s Security Services takes a holistic approach to protecting the availability, confidentiality, and integrity of information and knowledge capital for our customers. Information is an essential asset in today’s connected world. We approach your security services needs from a systems integration perspective, and protecting an organization’s significant information assets on an end-to-end basis. Please see Figure 1.
Security Services
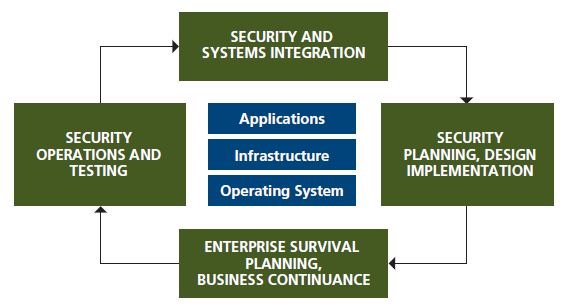
AIP US’s Security Services include:
- Security program design and strategy
- Security assessment and audit
- IT security policy design
- Vulnerability assessment and remediation
- Network firewall architecture and implementation
- Next generation firewall services – intrusion detection/intrusion prevention, malware filtering, and web security
- Email security
- Data backup and protection
- Endpoint protection and anti-virus/anti-malware
- Security information and event management (SIEM)
- Incident response
- Disaster recovery and business continuity planning
Our experienced security professionals can help you customize and implement a protection package that best suits your business requirements and helps keep mission-critical data available and protected against attack.

